In this blog I am going to explain how we can use use values saved in Azure Key Vaults can be used while building Azure Function .
First of all you need to have your Key Vault (https://docs.microsoft.com/en-us/azure-stack/user/azure-stack-key-vault-manage-portal?view=azs-1910) and an Azure Function Created(https://docs.microsoft.com/en-us/azure/azure-functions/functions-create-function-app-portal) in Azure.
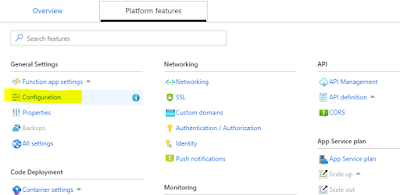
Once you have your Azure function, enable the managed service identity which will add an identity in your azure AD. To do this click on Platform Features->Identity
Now change the button from "Off to On" for System Identity
Once you enable the Identity, you will get the below message:
Now go back to Key Vault. Click on the Access Policies inside Key Vault:
Now Click on "Add Access Policy":
Now on "Add Access Policy" page click on the "Select Principal"
Now on the search pop up search for your azure function, for example here my Az Function name is "MyKeyVault" function
And now from "Configure from template" provide proper access that is required.
Now click "Add". Now click on "Secrets" and "Generate/Import Secrets" to save new "Secret Values" in Key Vault:
Once you add the secret, copy the secret identifier:
Now go back to Azure function and select configuration and add a new variable:
Here I am going to add a new Application Setting string "MyPat" and paste the secret identifier copied from key vault to the value text box as shown below:
@Microsoft.KeyVault(SecretUri=Secret Identifier from Key Vault)
@Microsoft.KeyVault(SecretUri=https://arunvarriardevops.vault.azure.net/secrets/myvault/123456789)
Once you add this now we can directly use these as system config values in our azure function as:
string MySecretKey= System.Environment.GetEnvironmentVariable("MyPAT");
Here System.Environment.GetEnvironmentVariable("MyPAT") will fetch the actual key vault secret and save it to the string MySecretKey.
I hope this helps.
First of all you need to have your Key Vault (https://docs.microsoft.com/en-us/azure-stack/user/azure-stack-key-vault-manage-portal?view=azs-1910) and an Azure Function Created(https://docs.microsoft.com/en-us/azure/azure-functions/functions-create-function-app-portal) in Azure.
Once you have your Azure function, enable the managed service identity which will add an identity in your azure AD. To do this click on Platform Features->Identity
Now change the button from "Off to On" for System Identity
Once you enable the Identity, you will get the below message:
Now go back to Key Vault. Click on the Access Policies inside Key Vault:
Now Click on "Add Access Policy":
Now on "Add Access Policy" page click on the "Select Principal"
Now on the search pop up search for your azure function, for example here my Az Function name is "MyKeyVault" function
And now from "Configure from template" provide proper access that is required.
Now click "Add". Now click on "Secrets" and "Generate/Import Secrets" to save new "Secret Values" in Key Vault:
Once you add the secret, copy the secret identifier:
Now go back to Azure function and select configuration and add a new variable:
Here I am going to add a new Application Setting string "MyPat" and paste the secret identifier copied from key vault to the value text box as shown below:
@Microsoft.KeyVault(SecretUri=Secret Identifier from Key Vault)
@Microsoft.KeyVault(SecretUri=https://arunvarriardevops.vault.azure.net/secrets/myvault/123456789)
Once you add this now we can directly use these as system config values in our azure function as:
string MySecretKey= System.Environment.GetEnvironmentVariable("MyPAT");
Here System.Environment.GetEnvironmentVariable("MyPAT") will fetch the actual key vault secret and save it to the string MySecretKey.
I hope this helps.